Kali Linux 1.0
When it comes to hacking, security, forensics thing like that, linux is the only and the preferred tool. Linux is very hacker friendly from ground up. But still there are distros that are more oriented towards assisting hackers. To name a few, backtrack, backbox, blackbuntu etc.
Backtrack is the most popular distro when it comes to penetration testing and security stuff. And now it has taken a new avatar called Kali Linux. Kali Linux is the new name of backtrack (version 5 rc3 was the last backtrack release).
Complete distro based on Debian
Kali Linux has been improved over Backtrack in many ways. Backtrack was kind of "Ubuntu + security tools placed in the /pentest directory". And due to this, to run any security tool first the user had to navigate to the pentest directory. This made updates difficult too, since the tools were not real installations that could be updated from synaptic.
Kali Linux is the new generation of the industry-leading BackTrack Linux penetration testing and security auditing Linux distribution. Kali Linux is a complete re-build of BackTrack from the ground up, adhering completely to Debian development standards.
Kali linux has everything installed like packages that can be updated from repositories. Kali Linux is based on Debian and is a complete distro in itself. To run any tool just type the command at the terminal and it would run.
Also there is no more need to type the startx command at boot, like in backtrack.

Download Kali Linux from the following url
http://www.kali.org/downloads/
It can be easily installed inside a virtualizer like Virtualbox. Infact I use it inside virtualbox only. Kali linux needs to run as root, and therefore its very secure to run it inside a virtual environment, or from a live media.
At the time or writing this post, kali 1.0.4 was the latest version
Backtrack had both a gnome and kde version available for download. However kali linux comes only in the gnome based build. However other desktops like xfce, kde can be easily installed from synaptic.
Default packages
Kali linux by default comes with plenty of security tools, all found in the "Applications > Kali linux" menu. Apart from that, there are very few packages. The following are available
1. Browser - Iceweasel 2. Mysql 3. Apache server 4. ssh server
Other productivity tools like openoffice/libreoffice, gimp etc are absent. But can be easily installed from synaptic.
Also, the gnome desktop of kali linux is gnome 3, but it appears like the classical gnome 2 desktop, because it is a hacked version.
Kali linux is configured to run as root. Even after installation to hard drive, it runs as root. This is necessary because many security tools like wireshark, nmap need to run as root.
Install to hard drive
Since kali linux is based on Debian, the boot menu provides options for a graphical or text based installer. Just choose any one and continue. The graphical installer is easier if you prefer.
You can either boot live and use it. Or start the installer to install it. Booting live is useful when used with a flash drive.
To install just follow the onscreen instructions like any other linux distro and the installation should work just fine. Unlike backtrack, kali boots into a proper display manager with login screen.
Kali Linux Top 10
Kali is packed with hundreds of tools placed in relevant categories like web application testing, sql injection, buffer exploitation, information gathering, server fingerprinting etc. However there is a separate menu that lists out the Top 10 tools.
The "Applications > Kali Linux" menu has a separate list for the top 10 security tools. These are the most useful, popular and featureful tools that find immense application in various kinds of tasks related to security like penetration testing, security analysis, application testing etc. Most of the tools are the best in their fields with no other similar equivalent or alternative.
Lets take a look at them.
1. aircrack-ng - Wi-fi sniffer and password cracker
aircrack-ng is the most popular software suite for sniffing the wireless network and cracking wep and wpa network passwords. It is used a lot in cracking wifi passwords and stealing internet connectivity.
The website describes it as
Aircrack-ng is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks, as well as the all-new PTW attack, thus making the attack much faster compared to other WEP cracking tools. In fact, Aircrack-ng is a set of tools for auditing wireless networks.
2. Burp Suite - Web application testing tool
Burp Suite is a very powerful and featureful web application testing tool that can be used to ping/poke/attack web applications in a number of ways to discover security flaws like sql injection, xss, csrf etc in them. It is a semi-automated tool that is very useful in analysing web applications and finding vulnerabilities.
Written in java and is cross platform. Includes features like modifying http requests, fuzzing http parameters, spidering hosts for possible urls etc. It comes in 2 versions, free and pro. The pro version is paid and includes some powerful features like automated scanning for vulnerabilities etc. Burp suite has been used to find vulnerabilities in websites like Facebook.
The website describes it as
Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application's attack surface, through to finding and exploiting security vulnerabilities.
3. THC Hydra - Brute force various protocols
Hydra is "A very fast network logon cracker which support many different services". Hydra is a simple brute forcing tool that can be used to crack the password of a number of services like ftp, http, vnc etc.
The following protocols are supported in version 7.4.2
Supported protocols: afp cisco cisco-enable cvs firebird ftp ftps http[s]-{head|get} http[s]-{get|post}-form http-proxy http-proxy-urlenum icq imap[s] irc ldap2[s] ldap3[-{cram|digest}md5][s] mssql mysql ncp nntp oracle-listener oracle-sid pcanywhere pcnfs pop3[s] postgres rdp rexec rlogin rsh sip smb smtp[s] smtp-enum snmp socks5 ssh sshkey svn teamspeak telnet[s] vmauthd vnc xmpp
Useful in cracking passwords of routers and other devices that are mostly configured with their default passwords.
It also has a gui called hydra-gtk/xHydra which is also included in Kali. Find it at the menu entry "Kali Linux > Password Attacks > Online Attacks > hydra-gtk"
4. John the Ripper - Crack password hashes
John the Ripper is the good old password cracker that uses wordlists/dictionary to crack a given hash. Can crack many different types of hashes including md5, sha etc. Has free as well as paid password lists available. Is cross platform.
John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords. Besides several crypt(3) password hash types most commonly found on various Unix systems, supported out of the box are Windows LM hashes, plus lots of other hashes and ciphers in the community-enhanced version.
Check out my previous tutorials on john the ripper
Cracking linux password with john the ripper
5. Maltego - Information gathering
Maltego is an open source intelligence and forensics application. It will offer you timous mining and gathering of information as well as the representation of this information in a easy to understand format.
Maltego is basically an information gathering tool, that can search the internet for publicly available information about a site or organisation. This helps in assessing the amount of information that has reached the public domain and if it poses a security threat. For example it can search google, twitter and other similar sources for the email addresses, domain names related to a particular site, and even names and details of individuals.
The basic idea is to find as much information as possible about someone or some organisation, from free sources on the internet.
6. Metasploit - Develop, maintain and launch exploits
Metasploit is the great exploitation tool that is used extensively in penetration testing. Metasploit is a framework that assists in developing, managing and using exploits. Exploits are organised in categories as individual modules. Users can add their own modules too.
Written in ruby and is cross platform. Has a web interface and a gui called armitage too.
Check out metasploit tutorials at
https://www.binarytides.com/category/hacking-2/metasploit-hacking-2/
7. Nmap - Port scanner
The industry's de facto port scanner. Nmap is one of the oldest and the powerful port scanning tool out there. Although it started out as a port scanner, it is capable of doing much more. Can scan large networks for alive hosts, port scan the hosts, get the daemon banners, get detailed information about the host including operating system etc.
Now nmap has a new feature called nmap scripts which allows developers to code scripts that can be used with nmap to automate certain kinds of scanning tasks.
Nmap has a gui called zenmap, that can be used to save scan settings as profiles and use them later. Nmap also includes a netcat type utility called ncat which is very featureful and is available for both windows and linux.
The website describes it as
Nmap ("Network Mapper") is a free and open source (license) utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts.
Nmap runs on all major computer operating systems, and official binary packages are available for Linux, Windows, and Mac OS X. In addition to the classic command-line Nmap executable, the Nmap suite includes an advanced GUI and results viewer (Zenmap), a flexible data transfer, redirection, and debugging tool (Ncat), a utility for comparing scan results (Ndiff), and a packet generation and response analysis tool (Nping).
Check out tutorials on nmap
Hacking with nmap - tutorial for beginners
Port scanning and network discovery with nmap
Information gathering with nmap scripts
8. Owasp Zap - Web application testing
The Zed Attack Proxy (ZAP) is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications.
Owasp ZAP is a tool similar to burp suite that is used to test web applications. Unlike burp suite, it is free and open source and led by owasp.
9. Sqlmap - Automatic sql injection
Sqlmap is the most infamous hacking tool of the century that allows any kid to hack and destroy any website that forgot to escape its sql queries properly. Its a completely automated exploitation tool for sql injection vulnerabilities. Most of the websites being hacked today have this tool behind the scene. It puts the hacker in complete control of the entire database of any web application.
Sqlmap is the "metasploit" of sql injections, and even better.
sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Check out tutorials on sqlmap
Sqlmap tutorial - Hacking with sql injection
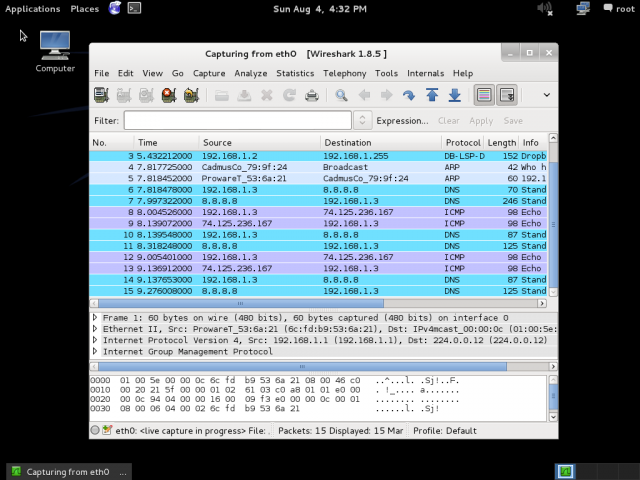
10. Wireshark - Packet sniffer and protocol analyzer
Wireshark is the most popular and powerful network sniffer and protocol analyzer out there. Available for both windows and Linux. It is a long history of evolution and has too many features. Useful in penetration testing to analyse the network and its traffic.
Wireshark is the world's foremost network protocol analyzer. It lets you capture and interactively browse the traffic running on a computer network. It is the de facto (and often de jure) standard across many industries and educational institutions.
Conclusion
So that was the list. If you too are fascinated by terms like hacking, penetration testing and network security then check out Kali linux. Can be easily installed inside virtualbox like any debian based distro.
In the next upcoming posts I shall write more about using various tools that are present in kali linux to learn and practise the art of penetration testing. Have fun till then.
Happy hacking !!


The top 10 is not containing SE-toolkit . I think you should have included ettercap,SE-toolkit in the list
What the hell is a security suite doing with ‘synaptic’ on board anyway?
to add/update packages ?
Pentoo is a joke, which has been beta for the past 8 years. You can safely ignore “Pentoo”.
At DEFCON, some of the hackers there were recommending Pentoo rather than Kali. I don’t know how/why Pentoo, but I thought it was worth mentioning.